Firmware Security
SmartBridges consists of a lot of firmware that is brings all the features that NET2GRID has to offer. This makes firmware updates essential for hardware to add new functionality, resolve bugs, and stay up-to-date with the latest security. On top of updates, the hardware needs to be hardened to prevent attackers from getting unauthorised access to Personal Identifiable Information. On this page all security measures can be found that are applied to all NET2GRID's hardware products.
Firmware Updates
The firmware server connection is secured via TLS/HTTPS. The gateway device verifies the TLS certificate provided by the server before sending the upgrade file request. Additionally, a unique key token is provided to the firmware server in the HTTPS in the body of the request. When a firmware file is marked as secure, the file will not be offered by the server to the client if the authentication token does not match.
Secure Boot
When an upgrade binary has been downloaded, the Elliptic Curve signature of the file is calculated using the public key stored on the gateway device. The new firmware can be booted if the provided key matches the calculated value. If the signature does not match, the update is rejected, and the previously booted firmware continues running. This process ensures that only firmware files signed with the private key known only to NET2GRID can be run on NET2GRID hardware.
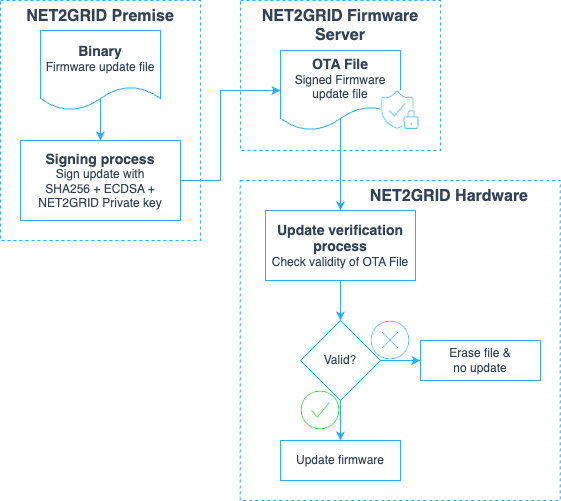
Flash Encryption
Program memory and non-volatile data are stored on an external SPI flash chip. The contents of this flash memory are encrypted with a unique key generated by the bootloader on the first boot.
Without access to the random flash encryption key, it is impossible to decode the contents of flash memory, even with physical access to the physical SPI pins of the flash memory chip.
Updated 6 months ago
